How One Developer Prevented a Global Cybersecurity Disaster
- Tachnology
In the world of cybersecurity, the smallest anomalies can signal the most significant threats. This was precisely the case when software developer Andress noticed something unusual—a spike in CPU usage that didn’t seem to belong. At first glance, it appeared to be a minor issue, but it was far from ordinary. What Andress had stumbled upon was not a simple glitch; it was a deeply embedded backdoor, a tool that cybercriminals could use to infiltrate millions of servers across the globe. Unbeknownst to him, his discovery would soon prevent a potentially catastrophic cyberattack.
The Hidden Dangers of Open-Source Software
To fully appreciate Andress' critical discovery, it’s essential to understand the role of open-source software in our digital infrastructure. Open-source software is code made available to the public, allowing anyone to view, modify, and improve it. While this collaborative model has led to the creation of many critical tools, it also presents risks. Unlike proprietary software, which is managed by dedicated teams within companies, open-source projects are often maintained by a small group of volunteers.
One such project is XZ Utils, a Linux-based data compression tool developed by Lasse Collin in 2005. XZ Utils is crucial to many Linux distributions, which are widely used to power everything from enterprise servers to supercomputers. However, Collin had been struggling to maintain the project due to personal health issues, and as is common in open-source projects, volunteers stepped in to help.
A Growing Cyber Threat in Disguise
In 2021, a contributor named Gatan joined the XZ Utils project and gradually became more involved. Over time, she gained enough trust within the community to be promoted to co-maintainer in June 2022, taking on even more responsibility for the project’s development. By 2023, she had full control over the project’s security alerts.
This, unfortunately, set the stage for what would later be discovered as a cleverly hidden cyberattack.
In early 2024, a new version of XZ Utils was integrated into a test version of Debian, a widely used Linux distribution known for its stability and security. During his routine tests on this version, Andress—an experienced developer at Microsoft—noticed that SSH, a secure shell protocol used for remote server access, was consuming far more CPU resources than expected. This was highly unusual, especially for such a core function. The sharp-eyed developer dug deeper and realized that the cause of this anomaly was a malicious piece of code embedded within XZ Utils.
A Malicious Backdoor Uncovered
Andress had discovered what cybersecurity experts call a "backdoor"—a vulnerability intentionally created within software to allow unauthorized access. In this case, the backdoor had been slipped into XZ Utils and could be exploited via SSH, giving hackers access to servers remotely. The stealthy nature of the attack meant that it had gone unnoticed for months, but thanks to Andress’ keen attention to detail, a massive breach was avoided.
On March 27, 2024, Andress alerted the Debian security team. Within days, the vulnerability was publicly exposed, and cybersecurity teams across the globe quickly took action. The compromised code had not yet been widely deployed, but it had the potential to affect millions of Linux servers, which run critical infrastructure for hospitals, universities, governments, and private enterprises.
The Backdoor
The backdoor discovered by Andress was highly complex and meticulously concealed. Unlike typical malicious code that might be detected in public repositories, this backdoor was not found in the XZ Utils GitHub repository at all. Instead, the malicious maintainer cleverly avoided detection by including it only in source code tarball releases, which are less scrutinized than the public repository. This tactic kept parts of the backdoor hidden, even as they were used during the build processes of dependent projects.
The backdoor was composed of several intricate components, introduced over multiple commits:
- IFUNCs in the build process: These were used to hijack the symbol resolution functions, allowing the malware to manipulate the way functions are linked during execution.
- Obfuscated shared objects: Hidden within test files to avoid detection.
- Malicious script execution: During the build process, a script was run to extract the shared object, which was excluded from the repository but included in release tarballs.
- Landlocking disabled: A security feature meant to restrict process privileges was turned off, further weakening security protections.
The backdoor's execution chain was equally complex and comprised multiple stages:
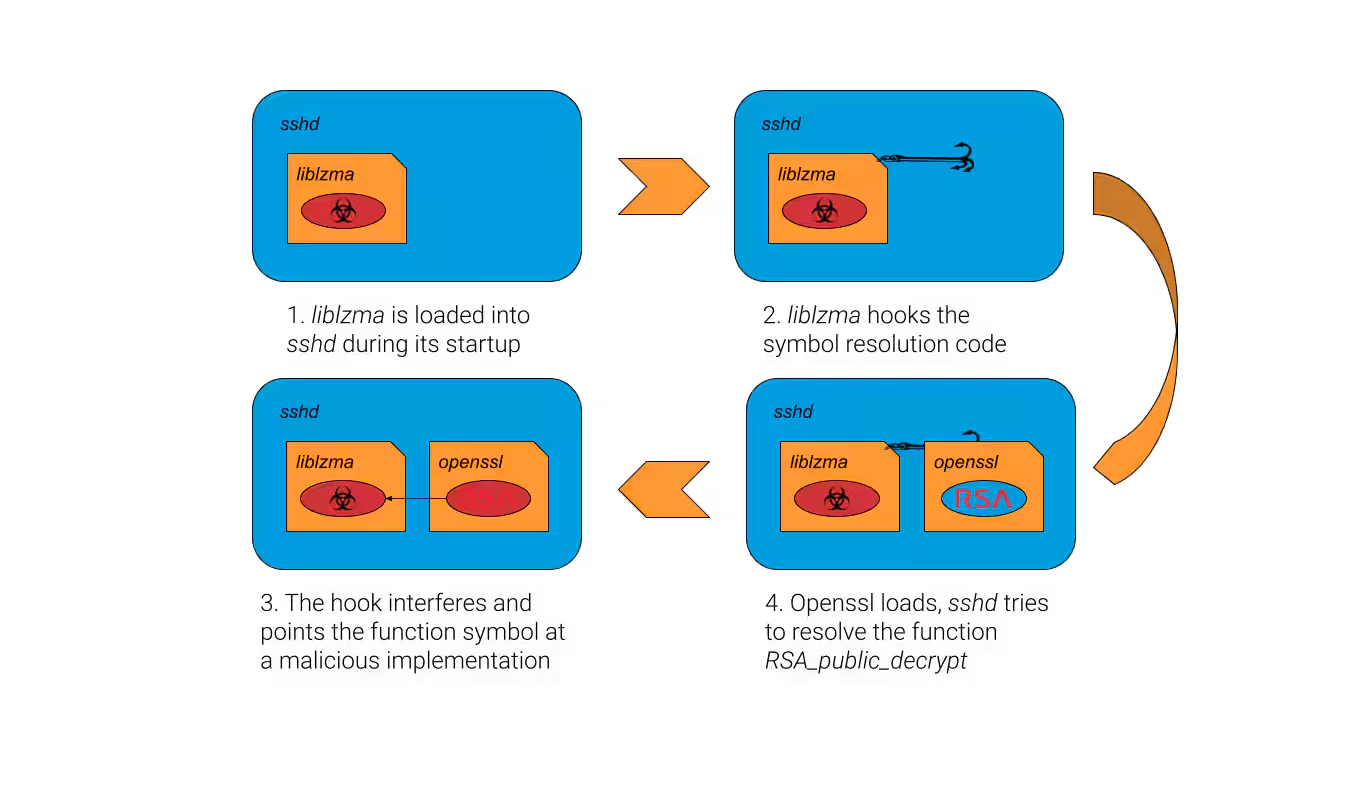
- Malicious build script: A script named
build-to-host.m4was executed during the library’s build process, decoding a "test" file namedbad-3-corrupt_lzma2.xzinto a bash script. - Bash script execution: This script performed a secondary decoding process on another file,
good-large_compressed.lzma, which in turn generated another script. - Shared object extraction: This final script extracted a shared object file,
liblzma_la-crc64-fast.o, which was then incorporated into the compilation process of the XZ Utils library.
This shared object interfered with the normal function resolution process, specifically targeting the SSH function RSA_public_decrypt. During process loading, the malicious library redirected the function pointer for RSA_public_decrypt to a malicious function. This malicious function was capable of extracting commands from an authenticating client's certificate and passing them to the system for execution, thereby achieving remote code execution (RCE) even before authentication took place.
For a more detailed breakdown, cybersecurity expert Thomas Roccia has published an infographic explaining this complex chain of execution, and further analysis is available in a post by Andres Freund on Openwall.
How a Global Cyberattack Was Prevented
The consequences could have been devastating had the backdoor made its way into stable Linux distributions. Hackers could have gained access to sensitive systems and data on a massive scale, potentially crippling essential services and critical industries. Linux powers a significant portion of the world’s digital infrastructure, from government institutions to major corporations, making this an unprecedented threat.
Within hours of Andress’ public report, teams of developers and cybersecurity experts scrambled to issue patches and neutralize the threat. The quick response prevented the malicious code from spreading to critical systems, effectively averting what could have been a large-scale cybersecurity disaster.
The Risks of Open-Source Software and the Need for Better Support
This near-miss highlights the vulnerabilities inherent in open-source software. While the open-source model fosters collaboration and innovation, it also leaves critical projects in the hands of a few volunteers who may lack the resources or support to maintain them effectively. In the case of XZ Utils, the backdoor had been inserted over an extended period, demonstrating the patience and sophistication of the attackers—potentially state-sponsored cybercriminals.
Open-source software is the backbone of much of the world’s digital infrastructure, yet it is often maintained as a labor of love by volunteers who contribute their time and expertise on the side. If we want to ensure the security of our digital systems, it’s imperative to provide more robust support and resources to these developers.
Conclusion: A Hero in Cybersecurity
Andress’ quick action and keen observation not only saved Linux from a major breach but also likely prevented a global cybersecurity catastrophe. The incident underscores the importance of vigilance in cybersecurity, particularly in open-source projects, where attackers can exploit gaps in oversight.
The world dodged a bullet this time, but the incident serves as a reminder that as our digital systems become more complex and interconnected, so do the threats we face. We must continue to support the open-source community and build stronger defenses to protect our critical digital infrastructure from future attacks.